#
Application Proxy
31 Oct 2023
Microsoft Entra ID (formerly Azure AD) provides an Application Proxy service that enables users to securely access on-premises applications from outside the organisations' internal network without the need for a VPN.
This document aims to help your organisation set up this Application Proxy for Pozi QGIS Server.
Required permissions:
- Administrator permissions on the on-premises server where QGIS resides
- An Entra ID service account with Application Administrator permissions
Please read carefully before executing the steps below.
This guide is based on (and refers to) steps outlined in the following Microsoft tutorial:
This document assumes that the first 2 steps (Prerequisites and Prepare your on-premises environment) of the tutorial have been followed and executed.
Entra ID's features and portal update frequently and this guide may not fully reflect the latest changes. Please contact us if you experience any inconstencies so we can update the documentation.
Visit the Microsoft Entra ID portal using https://entra.microsoft.com/
#
1. Install connector on on-premises server
The connector is a required piece of software that manages the outbound connection from the on-premises application servers to Application Proxy in Microsoft Entra ID. It runs as a service.
Tutorial: Install and register a connector

- Click on 'Download connector service', 'Accept terms & Download'
- Transfer downloaded file (e.g. 'AADApplicationProxyConnectorInstaller.exe') to the on-premises server
- Run the installer and follow the instructions



#
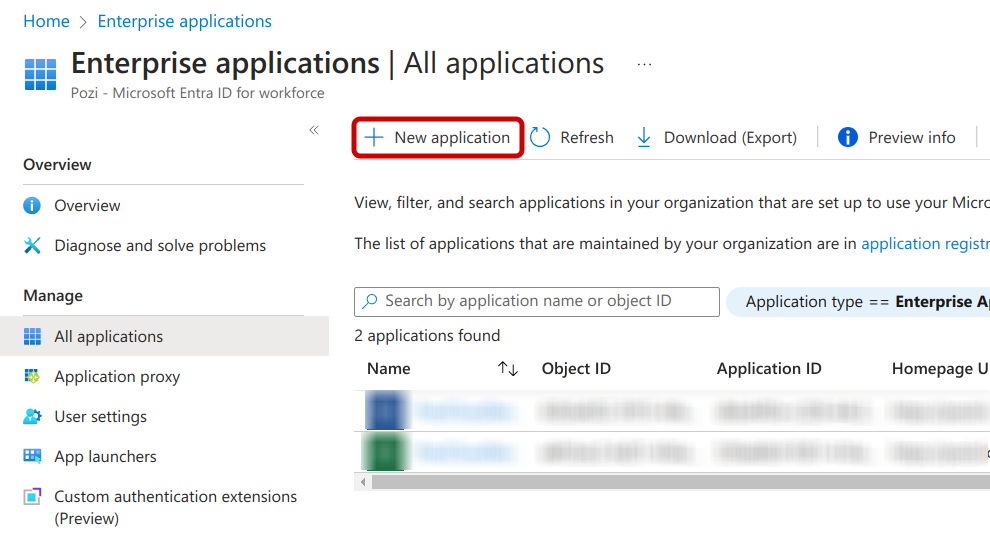
2. Add Pozi Server to Entra ID
This section describes how to add Pozi Server (on-premises app) to Entra ID platform as an Enterprise application.
Tutorial: Add an on-premises app to Microsoft Entra ID
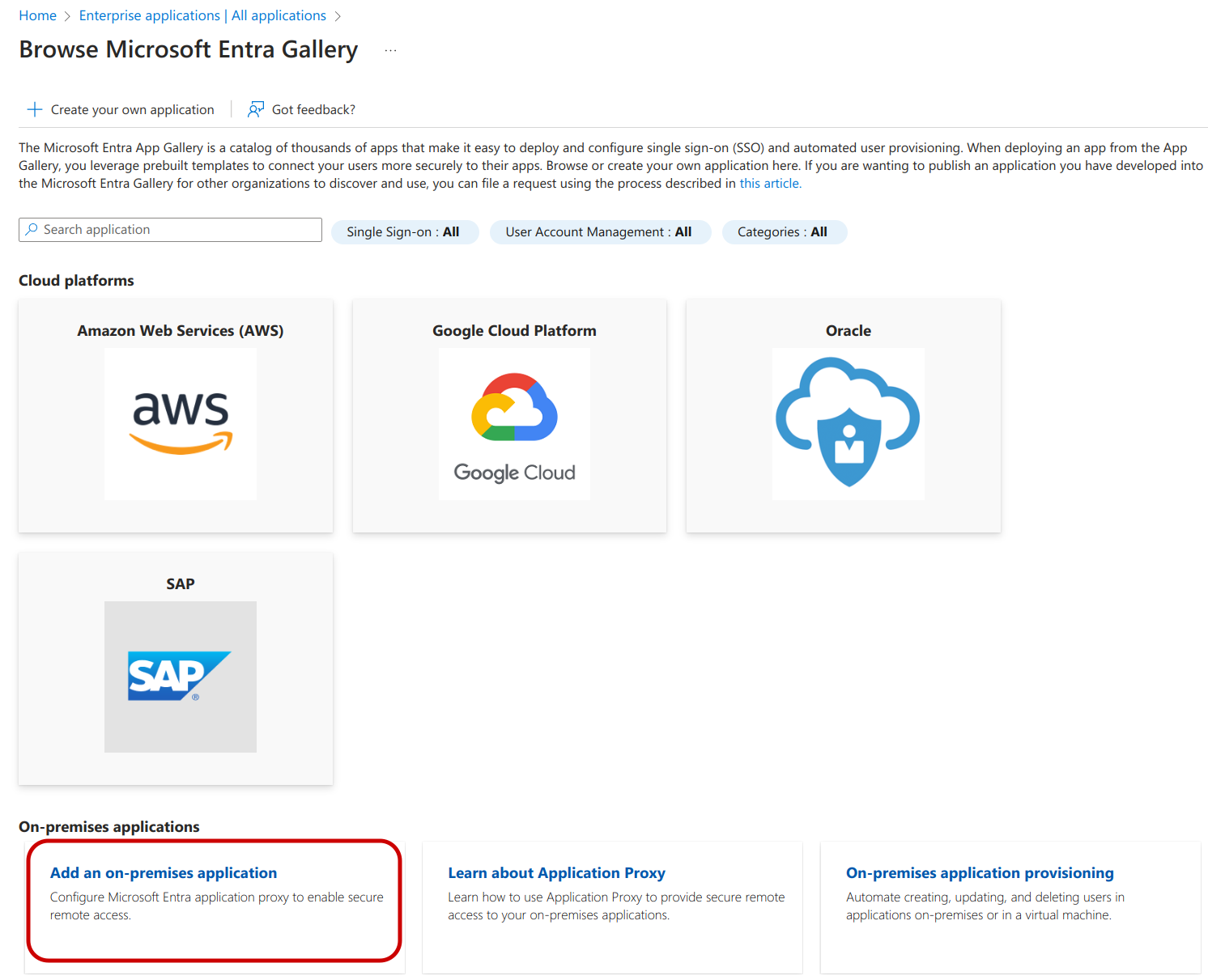
In the Add your own on-premises application section, provide the following information about your application:
#
Basic

Name :
Pozi Server(recommended). The administrator is free to choose an other name if that better suits the organisation's policies.Internal URL :
http://<internal-server-name>/pozi/. Replace<internal-server-name>with the actual name of the on-premises server on the internal network. This can belocalhostbut the actual server name is preferred.Example:
http://gis-server.local/pozi/To test internal URL on the internal network, opening the following URL in the browser should show a QGIS Server landing page:
http://<internal-server-name>/pozi/qgisserver/wfs3.htmlExample:
http://gis-server.local/pozi/qgisserver/wfs3.htmlExternal URL:
https://poziserver-<entra-application-client-name>.msappproxy.net.The
-<entra-application-client-name>.msappproxy.netpart is a name that has been given to the organisation MS Entra ID. The dropdown may reveal other domains like.<entra-application-client-name>.onmicrosoft.com. Please select the domain that your organisation prefers.The interface will show a fully qualified URL to access Pozi Server in grey text below the form fields.
Example:
https://poziserver-councilnamevicgovau.msappproxy.net/pozi/Pre Authentication:
Microsoft Entra ID. This will get Entra ID to handle the authentication process.Do not choose
Passthroughas that will allow any user (logged in or not) to access private resources from the server.
#
Advanced
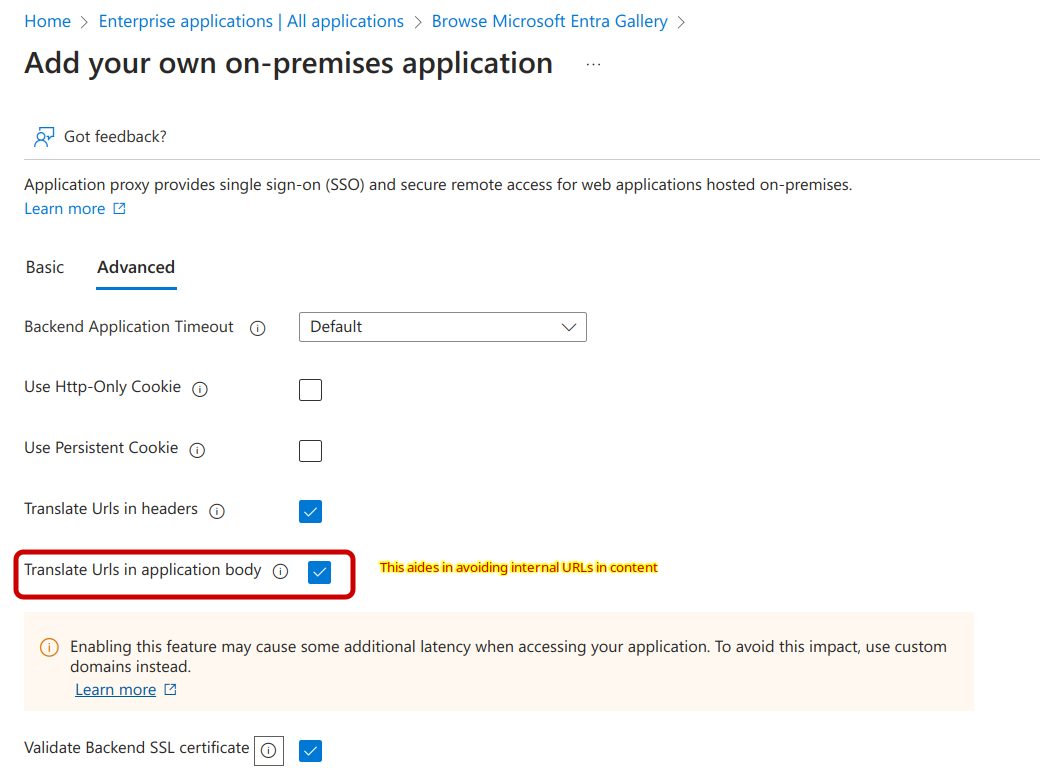
- Translate Urls in application body : checked. This allows Entra ID to translate internal URLs to their external counterparts.
#
3. Assign users
Tutorial: Test the application
It is recommended to assign an individual user first for testing before assigning additional users and/or groups.
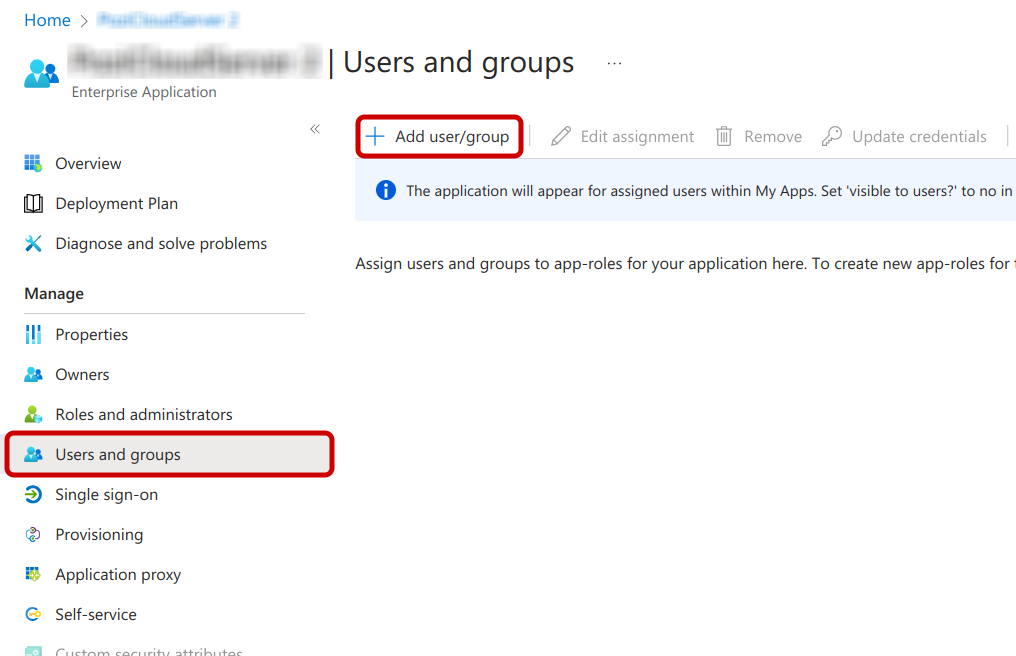
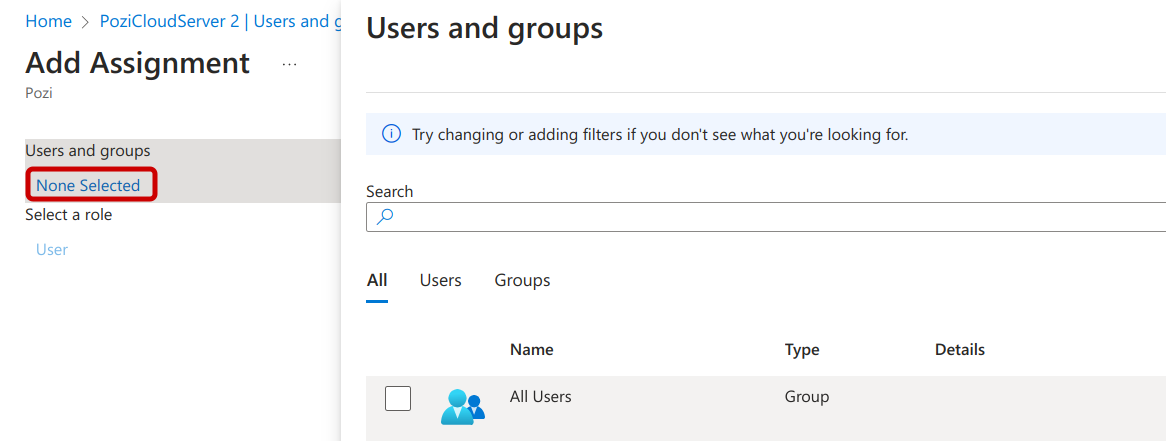
When configured correctly, a request from a logged-in user to Pozi Server through the Application Proxy URL should return the same result as within the local network.
Visiting following the Entra ID Application Proxy URL:
https://poziserver-<entra-application-client-name>.msappproxy.net/pozi/qgisserver/wfs3.html
...should return the same response as a local request to...
http://<internal-server-name>/pozi/qgisserver/wfs3.html
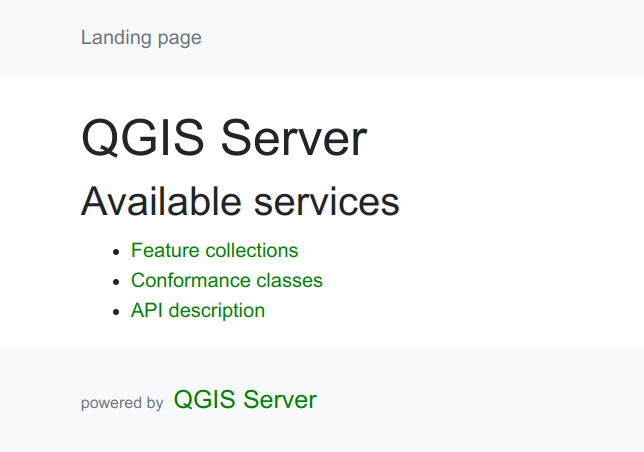
All going well, the QGIS landing page should now be visible when visiting the above Application Proxy URL.
It is recommended to try out the Application Proxy URL in an incognito browser window to verify that the page is not available to non-logged-in or anonymous users.
