#
Azure AD Application Proxy
Azure AD integration is a feature of the Pozi Enterprise Cloud offering.
Pozi's Azure AD Application Proxy integration enables your organisation's staff and other authorised users to access internal data sources in Pozi without needing to be connected to your network.
#
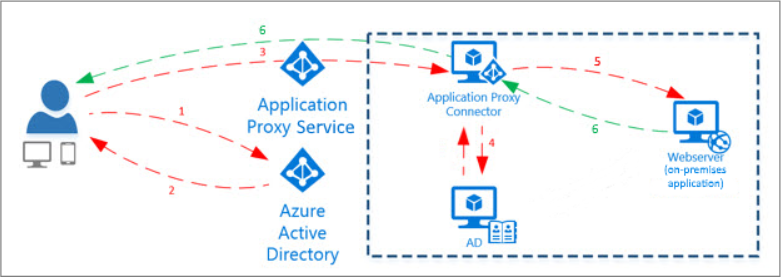
How it works
- user visits the dedicated Pozi Enterprise address (eg
<sitename>.enterprise.pozi.com) - Pozi app sends a request to client's MS App Proxy endpoint (eg
https://poziserver-<clientname>.msappproxy.net/pozi/qgisserver/wfs3.json) - if user is signed in to their Microsoft account, Pozi continues to load, and the user will have access to the internal datasets configured for Pozi within the organisation's app proxy
If the user is not already logged in, the browser is redirected to the Microsoft login page.
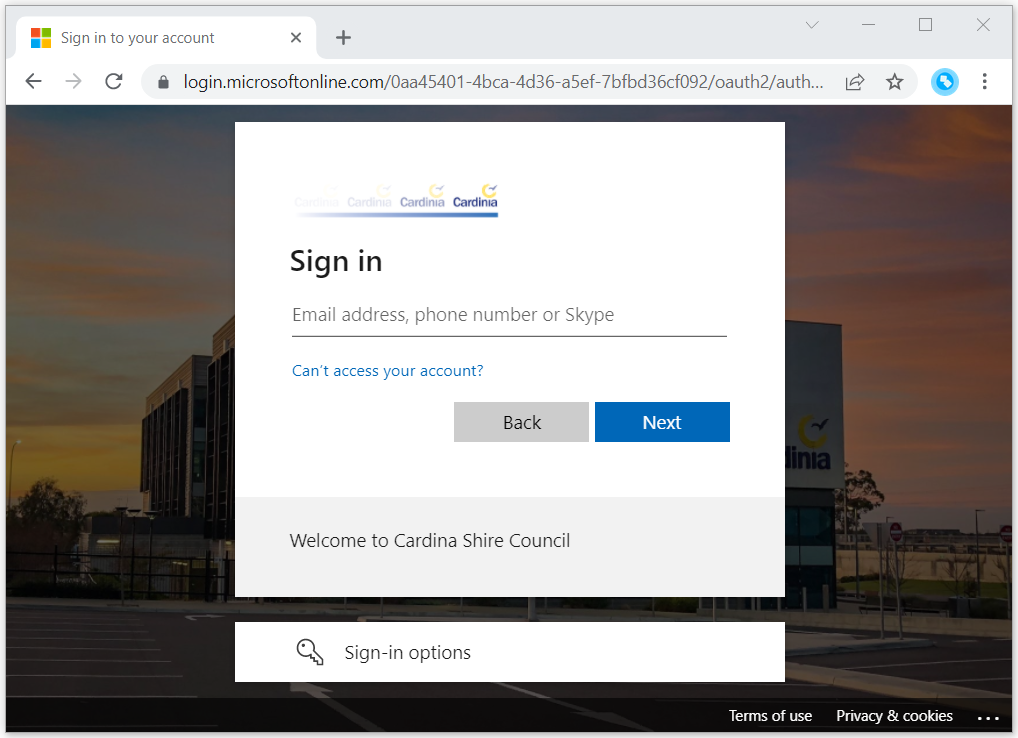
Once signed in, users will have access to internal datasets for as long their Microsoft account remains logged in.
#
Permissions
Whether a user can access private datasets is based on whether the user is given permission by the organisation to access the MS App Proxy endpoint that is dedicated for Pozi.
As long as the staff member or other authorised user has permission to access the MS App Proxy endpoint ( eg https://poziserver-<clientname>.msappproxy.net/pozi/), then they will have access to the internal datasets that have been configured within Pozi.
#
Site Url
Using <sitename>.enterprise.pozi.com enables a user to be authenticated before proceeding to the Pozi site. These users will gain access to the private datasets.
Public users should continue to use <sitename>.pozi.com. They will not be prompted to authenticate, and they will have access to only public data.
Example:
- Public Url:
https://<sitename>.pozi.com/ - Staff Url:
https://<sitename>.enterprise.pozi.com/
#
Configuration
See the Azure AD section in the Installation Guide.
